Navigating Risk Awareness: A Guide to Intentional Operational Security
In today’s ever-evolving landscape, operational security stands as a linchpin for organisational success. As the geopolitical disruptions of the past four years have underscored the need for resilience, the imperative to safeguard operations has never been more pressing. At the organisational level, policies and business continuity plans are in progress, but this urgency has yet to permeate to the project level. This disconnect between strategy makers and frontline execution is unnecessarily increasing project risk.
This piece delves into the critical importance of being intentional about operational security at both an organisational and project level, offering insights and strategies to navigate the complexities effectively.

What is Operational Security?
Challenges and Solutions to Operational Security
Operational security, or OPSEC, is a security and risk management process to systematically identify, assess and mitigate risks to organisational operations, assets, and personnel.
The operational security challenges an organisation faces often correlate with its size. In small to medium-sized entities, lack of resources and time forces people to adopt an optimistic belief that worst-case scenarios will not materialise. Meanwhile, in larger organisations, operational security is often undermined by the assumption that senior personnel will automatically intervene and save the day should any issues arise. These attitudes foster the misconception that operational security planning is merely a box-ticking exercise, rather than a genuine necessity.
Purpose-driven organisations, such as NGOs, journalist networks and television/radio productions, face the additional challenge of balancing the staff’s mission-centric outlook with security imperatives. Tight budgets, time constraints and mission priorities often compel individuals to cut corners and compromise safety measures.
However, the consequences of overlooking operational security are starkly evident when disruptive incidents occur. Without established plans and protocols, chaos tends to ensue in the initial stages of incident response, as individuals struggle to discern their roles and responsibilities.
Clearly communicating a strategic and systematic approach to operational security, both at the senior management and project levels, yields significant benefits. This is easier said than done.
How to Create an Operational Security Plan
Key Steps for Operational Security
Implementing operational security begins with a systematic approach tailored to each project or investigation. Having your project teams work through this simple framework and implement the following strategic principles and operational tactics, will increase the chance of success:
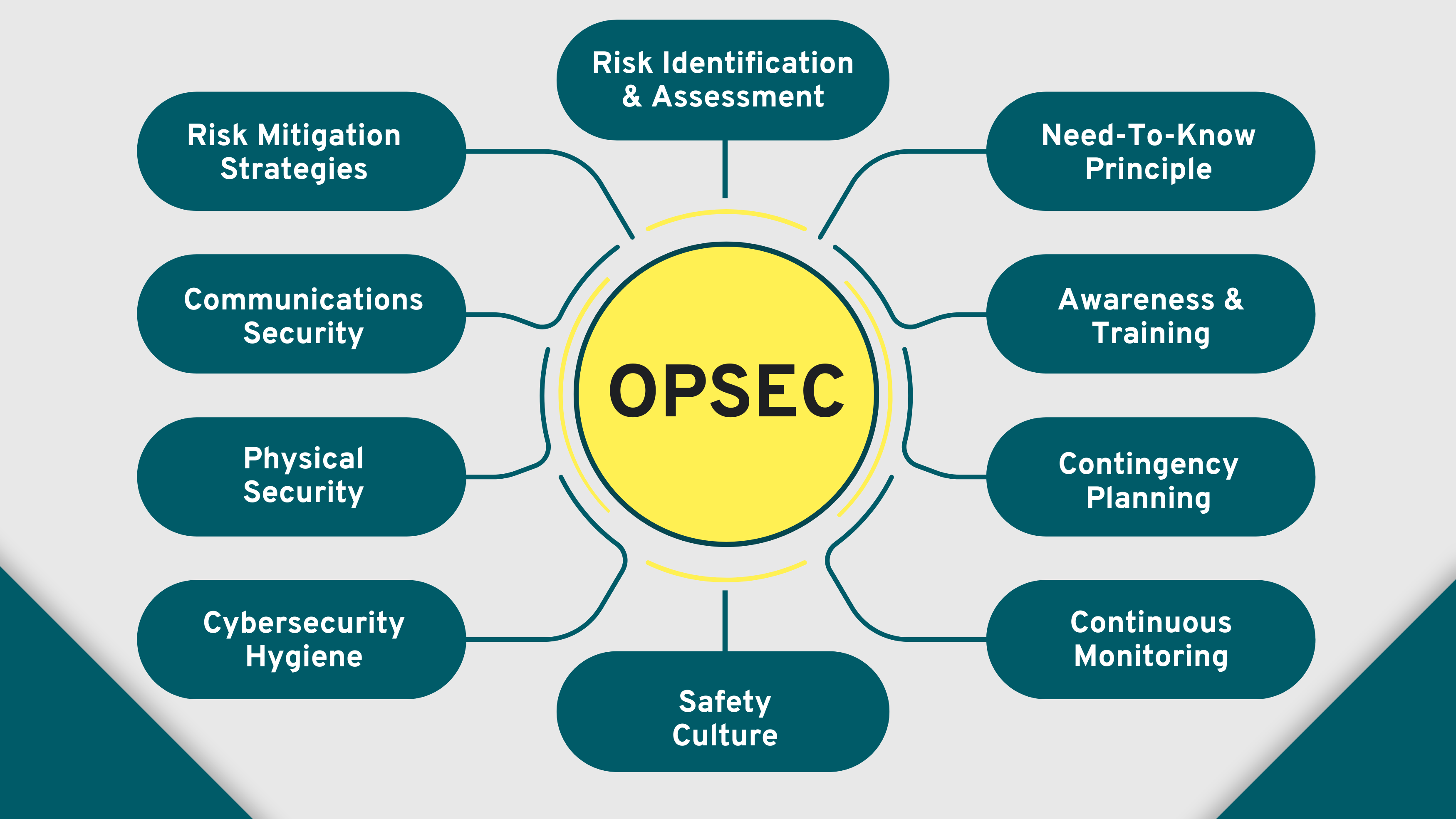
Mitigation Strategies
Developing and proactively implementing tailored mitigation strategies is crucial to minimising the identified risks. These strategies may include employing encrypted communication channels, diversifying routines for staff, implementing robust data security protocols, and conducting comprehensive security awareness training.
- Communications Security: Comms Security is paramount for safeguarding confidential information from unauthorised access. This involves establishing secure communication protocols, such as utilising encrypted messaging apps and refraining from using public Wi-Fi for sensitive communications. Clear guidelines should be defined regarding what information can be shared and how it should be transmitted.
- Physical Security: Physical security protocols are essential for safeguarding both staff and beneficiaries. Depending on the identified risks, a range of physical security measures should be implemented, such as varying travel routes, maintaining situational awareness, establishing protocols for emergencies, and ensuring safe working environments.
- Cybersecurity Hygiene: Good workplace cybersecurity is critical for protecting against digital threats and safeguarding sensitive information. The cornerstone lies in fostering cybersecurity awareness, focusing on critical topics including best practices for password management, recognising phishing attempts, and maintaining safe online behaviour. Additionally, organisations should utilise secure platforms for data storage and communication and consider implementing an information security management system.
Need-to-Know Principle
Access to sensitive information and resources should be granted based solely on a staff member’s designated role and responsibilities. Individuals should only have the minimum access necessary to perform their job responsibilities. By restricting access to sensitive information, organisations can mitigate the risk of unauthorised access. However, limiting access can create resentfulness from personnel who feel excluded, so the principle needs to be explained and reviewed frequently.
Contingency Planning
Contingency Planning involves crafting a comprehensive strategy for addressing potential breaches in operational security. This encompasses developing protocols for data recovery, establishing communication strategies for emergencies, and implementing evacuation procedures.
Risk Awareness & Training
Awareness and Training are vital components of operational security. Staff, and in particular managers, should be regularly trained on the OPSEC principles and best practices, ensuring everyone comprehends their role in upholding a secure environment.
Continuous Monitoring
Continuous Monitoring involves the ongoing review and updating of OPSEC protocols in response to the ever-evolving risk landscape and project developments.
Safety Culture
Robust operational security requires the fostering of a security-conscious culture within the organisation through senior management involvement and staff engagement. This involves actively encouraging staff to report any suspicious activity and to prioritise operational security measures in their daily operations.
Leading from the Top
Developing a culture of operational security requires intentional efforts, with senior management actively engaging in project planning. When senior managers are genuinely involved in risk planning, operational security becomes ingrained in projects from the start. Furthermore, when senior managers thoroughly examine and stress-test operational security mitigation suggestions, staff recognise that the process goes beyond mere box-ticking.
The Strategic Imperative of Operational Security
Intentional commitment implementing a security operations strategy is facilitated by a systematic framework across all levels of a business, with continual communication and reinforcement. At the same time, senior management engagement signifies that operational security is not just a mere lip service, but a valuable workflow that can reduce the risk of harm to colleagues and enhances project efficiency and overall organisational resilience.
Improve Your Operational Security Today
We work closely with our NGO and media clients to bridge the gap between senior management and frontline operations, building processes that meet the needs of all stakeholders. We have developed a comprehensive risk management bundle designed to structure your project risk approach and systematically assess and mitigate potential risks. At its core, this bundle includes:
- Drafting policy governance and standard operating procedures.
- Providing manager and staff risk training.
- Facilitating implementation of adequate insurance coverage.
- Establishing crisis management support.
- Providing operational security guidance at every stage of the project.
If you’re interested in learning more, contact us at RiskPal for risk management solutions and advice.